Yesterday, the UK Intelligence and Security Committee of parliament (ISC) released a report on the activities of China1 (and, specifically the Chinese Intelligence Services – ChIS) in relation to the security of the United Kingdom.
Having read the report, and been surprised by the breadth of activity, I was minded to write this blog to describe some of the tactics that can be used to target those of us with Public profiles. The Blog focusses on the UK ISC Report on China1 and the connection with LinkedIn.
The UK ISC Report on China1 discusses many different activities that ChIS have been previously involved in – both overt and covert. This blog post discusses the technology related findings within this report – and also means you don’t have to read the full 222 page document!
It should be noted that parliamentary committees can be perceived to have political agendas in relation to the work of the government. Therefore, I will deal purely with the factual elements of this report (specifically mining of information, and recruitment) and not the conclusions of the committee itself. Where statements are made, these have been cross-referenced to new articles and other resources. Additional sections have also been included based on other relevant reporting.
China’s Objectives
We don’t require conjecture to understand China’s objectives. These are laid out clearly in the Made in China 2025 policy document2. The stated objectives are to achieve influence and dominance in 10 different technology areas:
- Electric Cars
- Next-generation IT and Telecommunications
- Advanced Robotics and AI
- Agricultural Technology
- Aerospace Engineering
- New Synthetic Materials
- Advanced Electrical Equipment
- Emerging Biomedicine
- High-End Rail Infrastructure
- High-Tech Maritime Engineering
According to the ISC Report on China1 Chinese companies will do everything they can to retrieve data in a legal manner by acquiring companies or working with them (for example, a relationship in the 70s between Rolls Royce and China resulted in the transfer of IP for an engine design. China didn’t have the capability to build the engine at the time, but when they did they launched their own version of the Engine), building relationships with academics and universities (in the UK, for example, through the “Confucius Institutes”), and seeking targets through the use of Open Source information (e.g., scraping Social Media sites).
In some cases, however, more nefarious means are employed. The remainder of this document will focus on HUMINT (Human Intelligence) tactics – that have the potential to ensnare anyone reading this blog – and how these tactics have been used to mine information. In the following image the ISC Report on China1 illustrates an example process by which information is often gained.
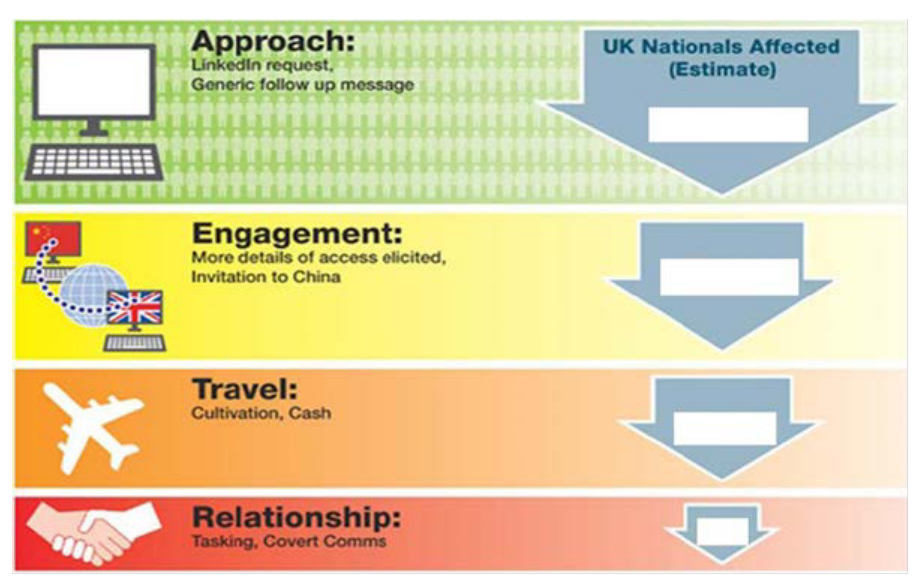
US Officials have also coined an acronym “MICE”, which stands for “Money, Ideology, Compromise, and Ego” to describe the means and motivations provided to gain sensitive information.
Before getting information from a target, however, it is necessary to be able to identify the targets that can be most fruitful (especially targets who work on the Top 10 strategic technology areas of interest to ChIS). This is discussed in the next section:
Human Mining
Two examples of the exfiltration of Human data (these examples are also known as APTs or “Advanced Persistent Threats”, often involving nation states) have been attributed to China. These attacks involved the OPM (The US Office for Personnel Management) and Experian (A credit reference agency)
OPM
According to Wired3, hackers infiltrated OPM systems between November 2013 and December 2014. The attack (which was based on a variant of the PlugX trojan) was discovered to be sending information to a website: opmsecurity.org, which was not owned by OPM. Technologists were shocked to discover that the owner of this website was none other than Steve Rogers. That’s right… Captain America (Captain America was not available for comment).

The usage of comic book names as owners of websites is something that has been seen before with these groups.
Now, OPM are responsible for running background checks for various US Government Departments. And during the attack period, the hackers exfiltrated up to 18 million background check documents. When one considers these documents often contain information on applicants that could be used to exert influence over them (for example: finances, substance abuse, previous psychiatric incidents, and risky sexual activity) this was clearly a treasure trove of information.
Not to rest on their laurels, the hackers then proceeded to extract 4.2 million employee files and 5 million employee fingerprint images.
Equifax
CNET describes4 how, In March 2017, an Apache Struts Vulnerability was used (only two days after the vulnerability was publicly announced) to install malware in Equifax’s system that would facilitate an uninterrupted 76 day period during which the hackers exfiltrated data. Frighteningly, the articles explains that this vulnerability was known to the company for months, but no action had been taken to remediate it.
Information was stolen from 51 databases – information (to varying degrees of detail) on 145 million US and 13 Million British citizens.
Again, this type of data can be incredibly important to organisations looking for vulnerable people (for example, reaching out specifically to people in positions of power and with very poor credit history).
In 2022, the FBI formally charged four Chinese military-backed hackers with the deed.
Given the above, it is clear that specific types of data have been stolen that has a use in leveraging targets for information that has unique and sensitive value.
It cannot be asserted, however, that this specific data led to the recruitment of “spies” on LinkedIn, however, it is indicative of the value that has been attributed to this data.
Other information is also publicly available through LinkedIn, and UK citizens have been criticised in the past by being too frank (and have been accused by the media of “bragging”) about sensitive organisations they work for.
LinkedIn Grooming
The ISC Report on China1 specifically calls out the use of LinkedIn by recruiters seeking sensitive information. The following section provides examples of when this has happened.
Germany uncovers network of fake LinkedIn profiles
As reported by the CSO5 In 2017, Germany uncovered 9 fake Chinese LinkedIn profiles and 3 Companies that sought to obtain information illictly. It was later reported by Der Spiegel6 that 10,000 German Citizens were targeted.

The information was surfaced after a 9 month German counter-intelligence investigation. In a break from tradition, the intelligence agency decided to make public their findings.
Jun Wei Yeo
As reported7 by the BBC In 2020, Jun Wei Yeo has been contacted through LinkedIn and was excited when he was asked to speak at a conference in Beijing in 2015.
During his visit he had conversations with people who worked for “Chinese Think Tanks”. These people turned out to be governmental think tanks… It was clear to Jun Wei that he was being groomed to provide sensitive information. His journey to becoming a Chinese agent had began (“Dickson” travelled to China 40 times between 2015 and 2019). He set up a fake Consulting Company on LinkedIn and used this as a cover to lure US targets:
Through this profile, he received more than 400 CVs8 from applicants for roles in his “Consultancy firm”, and passed relevant CVs (which would contain the roles they played in targeted organisations) onto his handlers.
Kevin Mallory
As reported9 by the BBC, Kevin Mallory had been approached by the “Shanghai Academy of Social Sciences” on LinkedIn. He had been working as an independent consultant, and was struggling to make ends meet, and was therefore a ripe target for handlers.
For $25k he sold secrets to China – including classified documents. However, he began worrying about being found out, and contacted the CIA to suggest he would help them “uncover” what was happening to him on LinkedIn. He was surprised during an interview when the FBI appeared, but continued his discussions nonetheless.
His handlers had provided him with a Mobile Phone with a secure messaging app through which they could communicate. Kevin, incorrectly, thought that because the app was “secure”, no message history would be kept. During the interview his phone inopportunely crashed, revealing his messages and thus unmasking his deep connection with his handlers.
The FBI formally arrested him in April 2017, as further described10 by the BBC in a follow-up article, and he was charged and incarcerated for 20 years.
Colonel Philip Ingram
In more positive news Colonel Philip Ingram, as recorded by the Mirror11, was approached by a Chinese Businessman on LinkedIn. The Businessman asked Colonel Ingram to fly to China and asked for “inside information” via an encrypted messaging application that could only be accessed by intelligence services. Colonel Ingram, 58, said: “Alarm bells started ringing when he said we would want to get information that isn’t easily accessible to anyone. He said, ‘You can guess the sort of stuff I’m after’”.
Thankfully, in this case, Colonel Ingram broke off communications and reported the incident, by which time the Businessman’s LinkedIn profile had vanished.
Conclusion
It is clear that, today, risks face everyone with a public presence, particularly those in sensitive industries. This Blog has explained how information on humans can be farmed, and how that information can be used by hostile state actors to obtain sensitive information.
In each of these cases, people have been tempted by the promise of free travel to China, money, and flattery. In other cases people have been subjected to blackmail through the use of honey-pots and other means.
It is crucial, therefore, to be aware of the methods employed so you can spot them. Here are some summary notes:
- Never reveal sensitive information in Public profiles
- If you work in an industry mentioned in the Made in China 2025 Strategy2, you may be more likely to be targeted
- Never engage with someone about your work without the consent of your employer
- Never enter into conversations about your work without first checking the credentials of the person asking that information (e.g., check their Network on LinkedIn and ask others they are connected to about how they know the person)
- Rarely is someone likely to offer you an all-expenses paid trip to another country to give a speech without an ulterior motive
- When at conferences abroad, be wary of what you say and to whom
- Open Source projects can be a source of IP and can be scraped with ease. Think carefully before sharing any IP in a public manner
- If you have reason to believe you are being groomed for information, help make sure the individual doesn’t simply move on to another person. In the UK, you can report incidents here: Report suspicious activity to MI5 – GOV.UK (www.gov.uk). In other countries, please refer to your local authorities
- And for goodness sake – if someone tells you one of your systems has a vulnerability – patch it!
Of course, the ISC Report on China1 mentions tactics and approaches that will likely pass most of us by, however, it is useful to always be fully aware of the tactics used.
Citations
1 ISC. (2023). Intelligence and Security Committee of Parliament, China Report. Intelligence Security Committee. https://isc.independent.gov.uk/wp-content/uploads/2023/07/ISC-China.pdf
2 Made in China 2025 – Wikipedia. (n.d.). Retrieved July 14, 2023, from https://en.wikipedia.org/wiki/Made_in_China_2025
3 Inside the OPM Hack, The Cyberattack that Shocked the US Government | WIRED. (n.d.). Retrieved July 14, 2023, from https://www.wired.com/2016/10/inside-cyberattack-shocked-us-government/
4 How the Equifax hack happened, and what still needs to be done – CNET. (n.d.). Retrieved July 14, 2023, from https://www.cnet.com/news/privacy/equifaxs-hack-one-year-later-a-look-back-at-how-it-happened-and-whats-changed/
5 Espionage: Germany unmasks fake Chinese LinkedIn profiles | CSO Online. (n.d.). Retrieved July 14, 2023, from https://www.csoonline.com/article/563859/espionage-germany-unmasks-fake-chinese-linkedin-profiles.html
6 Soziale Netzwerke: Geheimdienst enttarnt Fake-Spionageprofile – DER SPIEGEL. (n.d.). Retrieved July 14, 2023, from https://www.spiegel.de/politik/deutschland/soziale-netzwerke-geheimdienst-enttarnt-fake-spionageprofile-a-1182502.html
7 How a Chinese agent used LinkedIn to hunt for targets – BBC News. (n.d.). Retrieved July 14, 2023, from https://www.bbc.co.uk/news/world-asia-53544505
8 How a Singaporean man went from NUS PhD student to working for Chinese intelligence in the US – CNA. (n.d.). Retrieved July 14, 2023, from https://www.channelnewsasia.com/singapore/dickson-yeo-us-china-intelligence-singapore-nus-phd-711701
9 Kevin Mallory: The churchgoing patriot who spied for China – BBC News. (n.d.). Retrieved July 14, 2023, from https://www.bbc.co.uk/news/world-us-canada-46557096
10 Kevin Mallory: Ex-CIA agent jailed for spying for China – BBC News. (n.d.). Retrieved July 14, 2023, from https://www.bbc.co.uk/news/world-us-canada-48319058
11 British firms on alert after Colonel targeted by Chinese spies on LinkedIn – Mirror Online. (n.d.). Retrieved July 14, 2023, from https://www.mirror.co.uk/news/uk-news/british-firms-alert-after-colonel-28304749



